02/27/2024
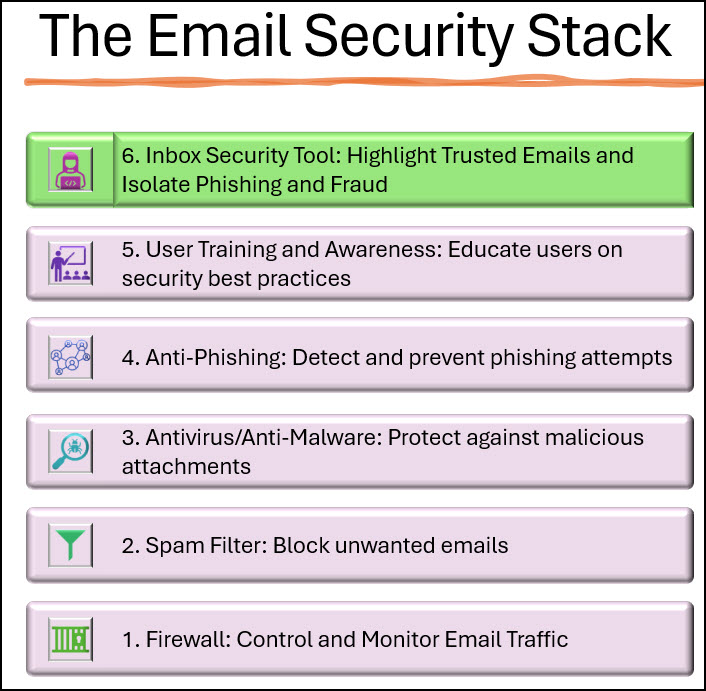
In our never-ending battle against cyber threats, all of us in the cybersecurity business have armed ourselves with formidable defenses to protect one of our most utilized channels of communication: email. Every organization uses these 5 layers of security:
5. User Training and Awareness: Educate users on security best practices
4. Anti-Phishing: Detect and prevent phishing attempts
3. Antivirus/Anti-Malware: Protect against malicious attachments
2. Spam Filter: Block unwanted emails
1. Firewall: Control and Monitor Email Traffic
No CISO would argue for removing any of these essential layers.
Yet, there exists a new sixth layer which will prove critical in the security stack: Verification in the Inbox.
This layer isn't about blocking or removing. It's about illuminating and endorsing. It differentiates the trustworthy from the treacherous, providing a beacon of safety in a potential sea of deceit.
Why is Layer 6 Necessary?
The first five layers work tirelessly to filter out the majority of threats. Yet, no system is impervious to BEC (Business Email Compromise) attacks. Layer 6 steps in to handle what might slip through by giving users a clear, visual affirmation of a message's integrity.
It also empowers the user by highlighting emails from trusted senders, while reinforcing the training users have received, enabling them to make informed decisions effortlessly.
Sophisticated phishing schemes can sometimes mimic legitimate communications, potentially deceiving even the most astute observer. Layer 6 helps to peel away the disguise, making the genuine unmistakable, while isolating phishing, fakes and fraud.
A 5 layered security approach has served us well, but given the emergence of million-dollar ransomware attacks, the addition of a tool to provide verification in the inbox is not just an enhancement: it's a necessity. It bridges the gap between automated defenses and human judgment, providing a robust safeguard that complements and strengthens existing measures.
CISOs need all the help they can get protecting the financial assets of an organization from ransomware thieves as well as the disruption caused by a successful attack. The power of this sixth layer is in its ability involve the user in threat protection by providing critical information about an email to the user, in a timely manner, at the point of attack in the inbox. That could mean the difference between a secure communication environment and a compromised one.
Just as user training is no longer considered optional, we believe that providing the user information to help differentiate the good from the bad messages right in the inbox will soon be a checklist item for all CISOs to help better protect their users and therefore to better protect the organization.
Blog Tags
BEC, Email Security